Due to the rapidly evolving technological generation in the world, there has been a great computer renaissance in society today. Through it, we see that it can lead the lives of people in the world and society as well as in a new direction. However, in today’s society, we can see there is a gap of citizens with human qualities. We must protect all our data and information as well as our privacy from these individuals or teams. This is because these parties are exposed to large-scale business principles and financial frauds, the theft of military and nuclear secrets, the theft of personal information from various organizations, and the uninterrupted surveillance of people’s day-to-day use of computers and mobile phones. Ultimately, by committing these disruptive acts, they commit great frauds and some people engage in such acts to make others suffer for their own self-satisfaction. So when discussing this, we should be aware of cybersecurity. Frederick Chang (2012) (former director of research at the U.S. National Security Agency, describes the interdisciplinary nature of cybersecurity) describes cybersecurity as follows.
“The science of cybersecurity offers many opportunities for advances based on a multidisciplinary approach, because, after all, cybersecurity is fundamentally about an adversarial engagement. Humans must defend machines that are attacked by other humans using machines. So, in addition to the critical traditional fields of computer science, electrical engineering, and mathematics, perspectives from other fields are needed.”
However, we can also define that, Cyber Security as the organization of resources, processes, and structures used to prevent misinterpretation and misuse of real property rights in cyberspace and cyberspace functional systems.
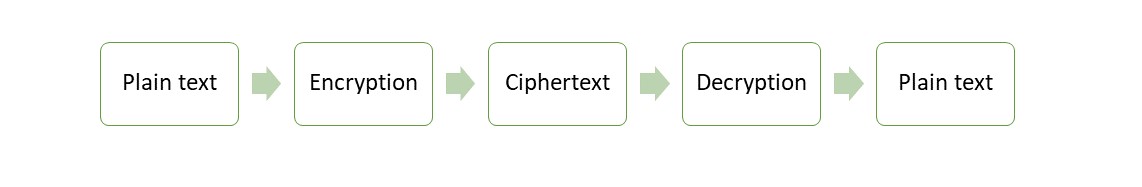
When we study Cybersecurity, Cryptography plays a key role. Cryptography is used to minimize data theft and to prevent stolen data from being misused by others. The peculiarity here is that an intermediary cannot understand the data we send. Because it is, encrypts the plain text into ciphertext according to mathematical algorithms. When the receiver received the ciphertext, the algorithm can decrypt it into plain text.
Figure 1. Cryptography process
Modern cypher implementations are based on the Cryptographic algorithm and a secret key, which the Cryptographic algorithm uses to modify data as it is encrypted. Cyphers with longer keys, measured in bits, may be more resistant to brute-force attacks, because the longer the key length, the more brute-force attempts are required to reveal the plaintext. While cypher strength is not always dependent on key length, security experts recommend that modern cyphers use keys ranging from 128 bits to 1,024 bits or more, depending on the algorithm and use case.
A key is such an important part of a Cryptographic algorithm that, in real-world ciphering, the key is kept secret rather than the algorithm. Strong cyphers are designed in such a way that, even if someone knows the algorithm, deciphering a ciphertext without the appropriate key should be nearly impossible. As a result, in order for a decrypting of the cypher to plain, both the sender and the receiver must have keys.
Classification of Cryptography
1. Symmetric Cryptography
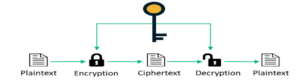
Symmetric cryptography uses the same key to encrypt and decrypt data.
Figure 2. Symmetric Cryptography Process
2. Asymmetric Cryptography
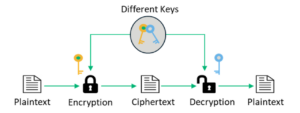
Asymmetric cryptography uses separate key pairs of public and private keys to encrypt and decrypt the data.
Figure 3. Asymmetric Cryptography Process
Symmetric Cryptography vs Asymmetric Cryptography
- Symmetric cryptography is based on sharing secrecy and asymmetric cryptography is based on personal secrecy.
- In the symmetric cryptography system, the number of keys needed for each user is 1. In an asymmetric cryptography system, the number of keys needed for each user is 2.
- In symmetric cryptography, symbols in plaintext and ciphertext are permuted or substituted. In asymmetric cryptography, plaintext and ciphertext are treated as integers.
- Symmetric cryptography is appropriate for long messages, and the speed of encryption/decryption is fast. Asymmetric cryptography is appropriate for short messages, and the speed of encryption/decryption is slow.
In summary, for cybersecurity, we have now surpassed all the major concepts surrounding symmetric vs. asymmetric cryptography. By now, queries about “what is the difference between symmetric and asymmetric encryption” and “symmetric key vs asymmetric key” should have been removed. Although the two are very different based on different mathematical structures, they have both found their application at different times. For example, it uses symmetric encryption to protect file contents and uses asymmetric encryption with digital signatures.