Our ongoing journey to ease the grind in SSDLC
Embarking on a Secure Software Development Life Cycle (SSDLC) journey last year marked a significant milestone for us – a shift towards enhanced security in our software development practices. While aligning with SOC2 compliance standards was a motivating factor, our commitment extended beyond mere compliance; we aimed to embed comprehensive security practices into every phase of development. The eBook featuring AI-powered SSDLC tools can be downloaded by clicking here.
This journey illuminated several challenges, notably the difficulty in finding a single tool capable of managing the entirety of the SSDLC. We realized that integrating security into our development lifecycle was as much about adopting the right tools as it was about changing mindsets and processes.
The advent of Artificial Intelligence (AI) has been a game-changer in this regard. AI-powered tools have transformed our approach, providing effective solutions to navigate and manage the complexities of modern software development. From automating routine tasks to proactively identifying potential security risks, AI has enabled us to foster a culture where security, efficiency, and quality coexist in every line of code we write.
In this article, we’ll delve into how integrating AI into the SSDLC has addressed our challenges. We’ll explore each phase—Requirements Gathering, Design, Development, Testing, Deployment, and Maintenance and Monitoring—and discuss the AI-powered tools that have been instrumental in enhancing our security posture and development efficiency.
I’m looking forward to sharing the ongoing positive changes and advancements within our team as we continue this journey toward a more secure and efficient development process.
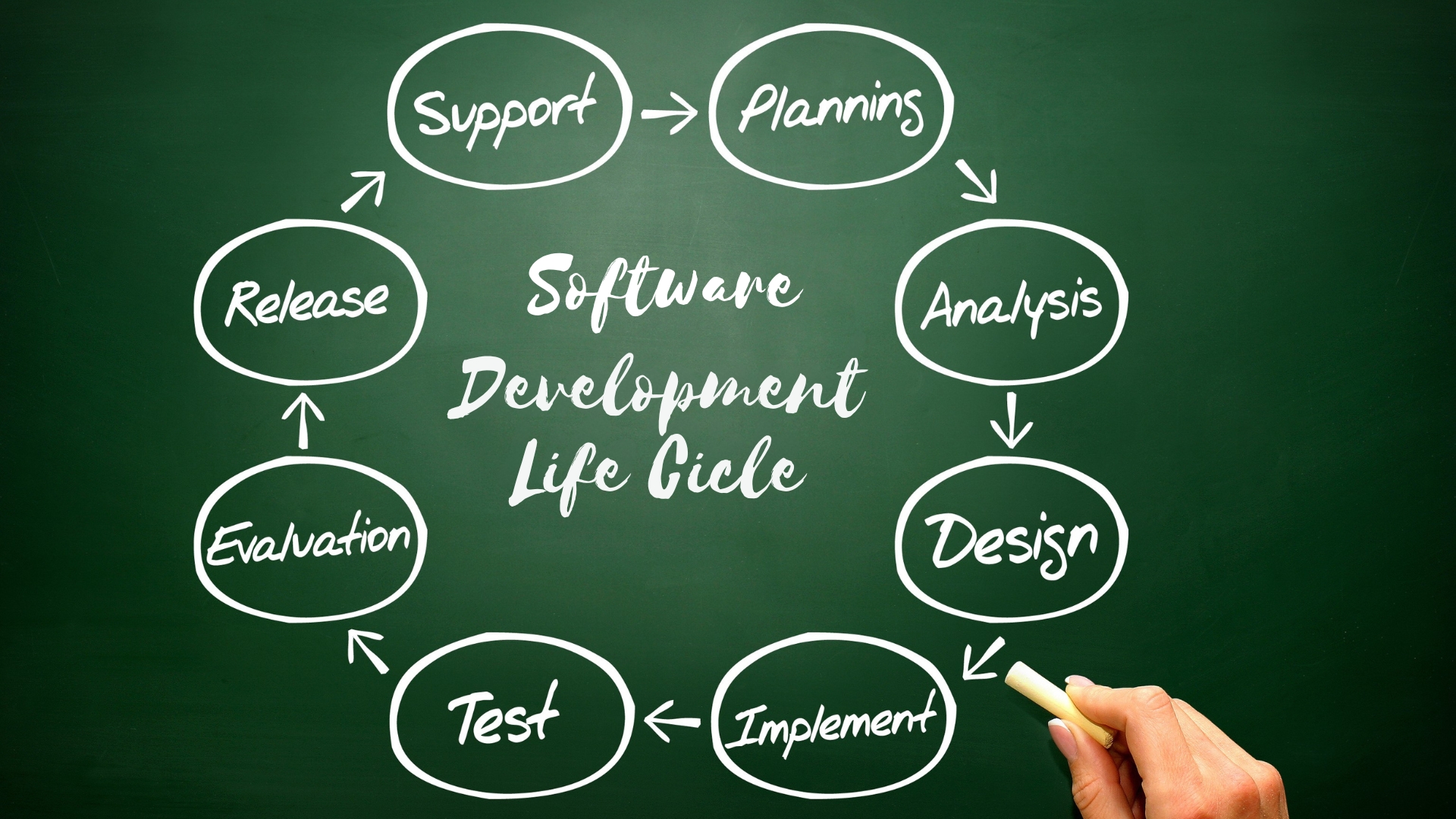
SDLC Explained
The Software Development Life Cycle (SDLC) is a structured framework that outlines the processes involved in creating, deploying, and maintaining software. It provides a systematic approach to software development, ensuring that the final product meets the specified requirements, is delivered on time, and stays within budget. The primary goal of SDLC is to produce high-quality software that satisfies customer needs and is reliable, efficient, and cost-effective.
Major Components of SDLC:
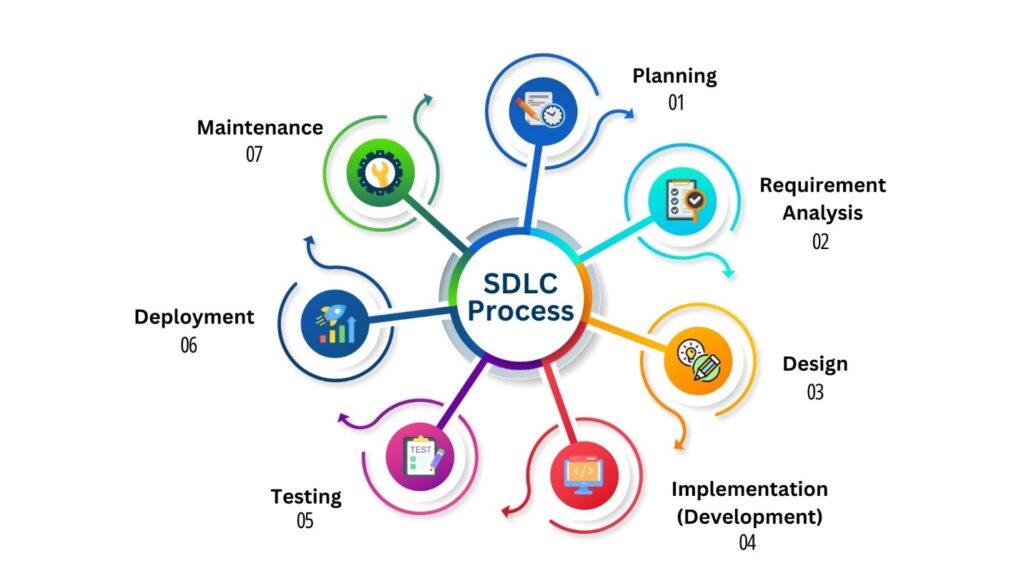
Planning:
The planning phase is where the groundwork for the project is established. This involves defining the project scope, objectives, and identifying the resources required. A feasibility study is often conducted to assess the viability of the project from technical, economic, legal, and operational perspectives.
Activities:
- Defining project goals and objectives.
- Estimating costs and resources.
- Identifying potential risks and mitigation strategies.
- Developing a project schedule with milestones.
Requirement Analysis:
In this phase, the development team gathers detailed information about the software requirements from stakeholders, customers, and users. The goal is to understand what the software must do (functional requirements) and the conditions it must meet (non-functional requirements).
Activities:
- Conducting interviews, surveys, and workshops.
- Documenting requirements in Software Requirement Specifications (SRS).
- Creating use cases and user stories.
Design:
The design phase translates the requirements into a blueprint for constructing the software. It involves planning the software architecture, user interfaces, system interfaces, and data models.
Activities:
- Defining system architecture (high-level design).
- Creating detailed design specifications (low-level design).
- Designing databases and data flow diagrams.
- Developing prototypes or mock-ups.
Implementation (Development):
This phase involves the actual coding and development of the software components according to the design specifications. Developers write code in the chosen programming languages, following coding standards and best practices.
Activities:
- Writing and compiling code.
- Conducting unit testing on individual components.
- Integrating modules into a cohesive system.
Testing:
The testing phase is critical for identifying defects and ensuring the software meets quality standards. It verifies that the software functions as intended and is free of bugs.
Activities:
- Integration Testing: Ensuring that combined modules work together correctly.
- System Testing: Testing the complete and integrated software for compliance with requirements.
- Functional Testing: The system is tested to ensure it performs according to the specifications.
- Regression Testing: Verifies that recent changes have not caused new bugs in areas of the software that were previously functioning correctly
- Non-Functional Testing: Tests such as performance, security, and usability testing are conducted
- Acceptance Testing: Validating the software with the end-users to ensure it meets their expectations.
- Performance and Security Testing: Assessing the software’s performance under various conditions and its resistance to security threats.
Deployment:
In the deployment phase, the software is released to the production environment where users can start utilizing it. This may involve deploying the software to servers, app stores, or distributing it directly to users.
Activities:
- Preparing the production environment.
- Deploying the software application.
- Conducting smoke tests to ensure basic functionality.
- Providing user training and documentation if necessary.
Maintenance:
Maintenance involves ongoing support and enhancement of the software after deployment. It ensures the software continues to function correctly and adapts to changing user needs or environments.
Activities:
- Corrective Maintenance: Fixing bugs that were not discovered during testing.
- Adaptive Maintenance: Updating the software to work with new hardware or software environments.
- Perfective Maintenance: Enhancing functionalities based on user feedback.
- Preventive Maintenance: Making changes to prevent future issues.
By following these structured phases of the SDLC, software development teams can:
- Improve Quality: Systematically addressing each aspect of development reduces the likelihood of defects and enhances overall software quality.
- Manage Time and Costs: Detailed planning and continuous monitoring help keep the project within the estimated timeline and budget.
- Ensure Customer Satisfaction: Involving stakeholders throughout the process ensures that the final product meets or exceeds customer expectations.
- Facilitate Communication: Clear documentation and defined processes improve communication among team members and stakeholders.
What is the meaning of SSDLC?
The Secure Software Development Life Cycle (SSDLC) is an extension of the traditional Software Development Life Cycle (SDLC) that integrates security practices into every phase of the software development process. The focus is on proactively identifying and mitigating security risks to ensure that software is secure from the outset, rather than treating security as an afterthought. By embedding security considerations throughout the development lifecycle, SSDLC helps organizations build robust, reliable, and trustworthy software products.
Why SSDLC is Necessary
The necessity of SSDLC arises from the increasing sophistication and frequency of cyber threats in today’s digital landscape. Traditional software development models often prioritize functionality and performance, with security checks performed only towards the end of the process or after deployment. This reactive approach can leave software vulnerable to attacks, leading to data breaches, financial losses, legal liabilities, and damage to an organization’s reputation.
By adopting SSDLC, organizations can achieve the following benefits:
Identify and Mitigate Risks Early:
- Cost-Effective Solutions: Addressing security issues early in the development process is more efficient and less costly than fixing vulnerabilities after deployment.
- Reduced Attack Surface: Early risk identification allows for the implementation of robust security measures, minimizing potential vulnerabilities.
Ensure Compliance:
- Regulatory Adherence: Many industries have strict regulatory requirements for data security and privacy, such as GDPR, HIPAA, SOC2, ISO, PCI DSS etc. Adhering to SSDLC process ensures that compliance standards are met.
- Avoid Penalties: SSDLC helps organizations meet these compliance standards, avoiding hefty fines and legal consequences.
Enhance Software Quality:
- Secure Coding Practices: Implementing secure coding standards improves overall code quality and reduces the likelihood of bugs and vulnerabilities.
- Reliability and Stability: Security-focused development leads to more stable and reliable software applications.
Prevent Financial Losses:
- Avoid Data Breaches: Proactive security measures completely arrest risk of cyber attacks that otherwise would lead to unnecessary expenses associated with regulatory fine, legal actions.
- Business losses: Security breaches can disrupt business operations, causing revenue loss from downtime and operational inefficiencies.
- Protect Reputation: Maintaining strong security practices helps preserve customer trust and brand reputation.
Build Customer Trust:
- Confidence in Security: Customers are more likely to trust and engage with software that is known to be secure.
- Competitive Advantage: Demonstrating a commitment to security can differentiate a company in the marketplace.
Major Components of SSDLC
Integrating security into each phase of the SDLC transforms it into an SSDLC. The major components include:
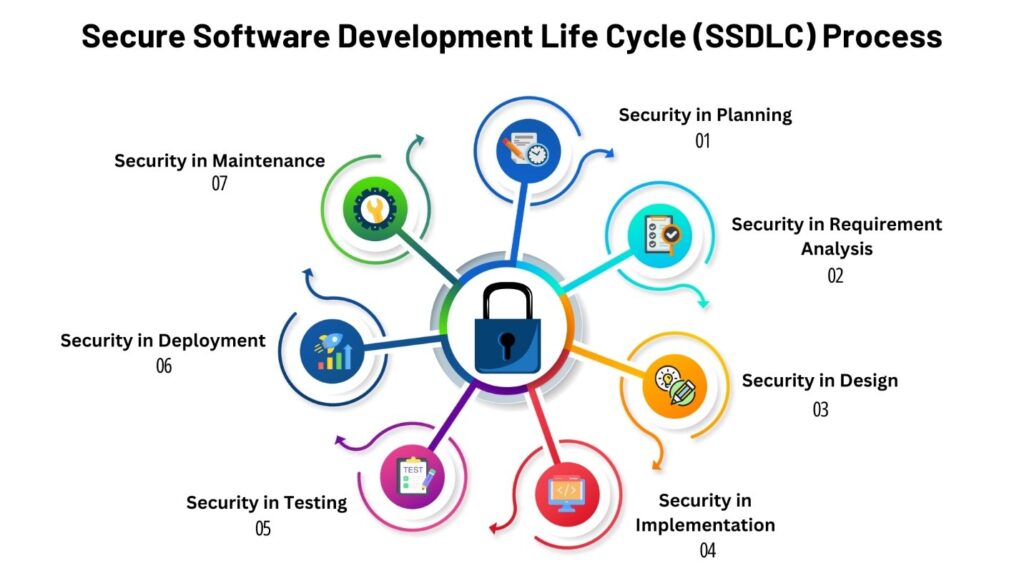
Security in Planning:
- Security Considerations: Identify security objectives, policies, and compliance requirements.
- Scope Definition: Clearly define the security scope in line with business goals.
- Resource and Cost Estimation: Allocate budget and resources specifically for security activities.
Security in Requirements Analysis:
- Understanding Security Needs: Gather and analyze security requirements alongside functional requirements.
- Threat Modeling: Begin initial threat modeling to identify potential security risks and attack vectors.
- Regulatory Compliance: Ensure that all legal and regulatory security requirements are identified and documented.
Security in Design:
- Incorporate Security into Architecture: Embed security controls and best practices into the system design.
- Design Principles: Apply secure design principles such as least privilege, defense in depth, and fail-safe defaults.
- Threat Modeling Refinement: Update threat models based on design decisions to address new potential vulnerabilities.
Security in Implementation (Development):
- Coding Standards: Adopt and enforce secure coding standards and guidelines.
- Static Code Analysis: Use automated tools to detect security vulnerabilities in the code during development.
- Code Reviews: Conduct peer reviews with a focus on identifying security flaws.
Security in Testing:
- Dynamic Analysis: Perform dynamic application security testing (DAST) to find runtime vulnerabilities.
- Penetration Testing: Simulate attacks to identify security weaknesses that could be exploited.
- Security Regression Testing: Ensure that new code changes do not introduce new vulnerabilities.
Security in Release and Deployment:
- Secure Configuration Management: Ensure that all system configurations are secure and documented.
- Security Checklists: Use deployment checklists to verify that all security measures are in place.
- Vulnerability Assessment: Conduct final security assessments before the software is released.
Security in Maintenance and Monitoring:
- Ongoing Security Updates: Regularly update the software to patch new vulnerabilities.
- Incident Response Planning: Develop and maintain an incident response plan to handle security breaches.
- Continuous Monitoring: Implement monitoring tools to detect and respond to security threats in real time.
Best Practices for Implementing SSDLC
Security Training and Awareness:
- Educate Team Members: Provide training for developers, testers, and stakeholders on secure development practices and emerging threats.
- Promote a Security Culture: Encourage a mindset where security is everyone’s responsibility.
Use of Security Tools:
- Automated Security Testing: Integrate security testing tools into the development pipeline for continuous assessment.
- AI-Powered Solutions: Leverage AI and machine learning tools for threat detection and vulnerability management.
Adopt DevSecOps Practices:
- Collaboration Across Teams: Foster collaboration between development, security, and operations teams to ensure seamless integration of security practices.
- Automation: Automate security checks within the CI/CD pipeline to catch issues early.
Regular Audits and Assessments:
- Third-Party Audits: Engage external experts to evaluate the security posture of the software.
- Internal Reviews: Conduct regular internal audits to ensure compliance with security policies.
Policy and Compliance Management:
- Define Clear Policies: Establish and enforce security policies and procedures.
- Stay Updated on Regulations: Keep abreast of changes in regulatory requirements and adjust practices accordingly.
Why are SDLC and SSDLC Important?
In our increasingly digital world, software is integral to virtually every aspect of business and daily life, making its development and security critically important. The Software Development Life Cycle (SDLC) provides a structured framework for creating functional and efficient software that meets user needs and performs reliably. However, as cyber threats become more sophisticated and frequent, ensuring functionality alone is insufficient. The Secure Software Development Life Cycle (SSDLC) enhances the traditional SDLC by integrating security practices into every phase of development. This proactive approach ensures that security is not an afterthought but a fundamental component of the software’s design and implementation. Together, SDLC and SSDLC enable organizations to develop robust, reliable, and secure software solutions. By understanding and applying these principles, we can better navigate the evolving challenges of technology, ultimately contributing to a safer and more efficient digital landscape.
AI in SSDLC
Integrating Artificial Intelligence (AI) into the Secure Software Development Life Cycle (SSDLC) revolutionizes the approach to software development by embedding advanced security measures and efficiency enhancements at every stage. AI-powered tools and techniques amplify the capabilities of developers and security professionals, automating routine tasks, providing intelligent insights, and proactively identifying potential vulnerabilities. This synergy not only streamlines development processes but also fortifies them against emerging cyber threats. By adopting AI within the SSDLC, organizations can accelerate development timelines, ensure compliance with security standards, and produce robust, reliable software that is secure by design. The fusion of AI and SSDLC represents a significant advancement in building resilient software systems in today’s complex digital landscape.
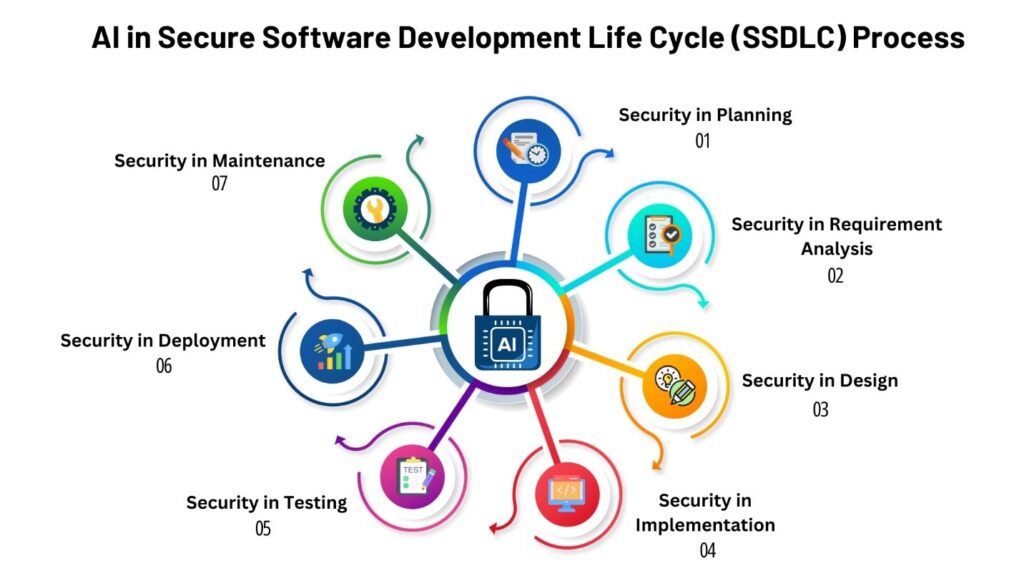
The Role of AI in SSDLC
Integrating Artificial Intelligence (AI) into SSDLC can further enhance security by:
- Automating Threat Detection: AI tools can analyze code and system behavior to identify potential threats more quickly than manual processes.
- Predictive Analysis: Machine learning models can predict potential vulnerabilities based on patterns in code or system configurations.
- Efficient Testing: AI-powered testing tools can simulate complex attack scenarios, providing more thorough security assessments.
- Continuous Monitoring: AI systems can monitor applications in real time, detecting anomalies and responding to threats promptly.
Requirements Gathering Phase:
In the initial phase of the Secure Software Development Life Cycle (SSDLC), AI plays a pivotal role in identifying and defining security requirements aligned with project goals and compliance standards. AI-powered tools enhance this process by analyzing vast amounts of data to extract pertinent security needs and potential risks.
By integrating these AI tools, organizations adopt a “security-first” mindset from the very beginning. AI aids in promoting developer awareness of security needs, ensuring that all necessary security requirements are identified and integrated from the outset. This proactive approach minimizes the risk of security issues arising later in the development process, saving time and resources.
Design Phase:
In the design phase, AI assists in translating requirements into secure and efficient architectural designs. AI-powered tools analyze proposed architectures for potential threats, suggest mitigation strategies, and recommend optimal design patterns to enhance security.
By incorporating these AI-driven tools, designers can proactively identify and mitigate security risks. AI aids in embedding security into the design, reducing the likelihood of vulnerabilities being introduced during later stages and helping build resilient software systems.
Development Phase:
The development stage is where AI significantly enhances efficiency and security. AI-powered coding assistants play pivotal roles in this phase. These tools leverage machine learning models trained on vast code repositories to provide intelligent code suggestions, auto-completion, and even generate code snippets based on context. They help developers write code more efficiently, adhere to best practices, and reduce the likelihood of introducing security vulnerabilities.
In addition to coding assistance, AI-driven code analysis tools are essential for embedding security within the development process. Some AI tools perform real-time static code analysis, identifying vulnerabilities and suggesting immediate fixes as developers write code. Some tools employ machine learning to detect code defects, security issues, and provide recommendations for code optimization.
By integrating these AI tools into the development workflow, developers can focus on complex problem-solving while AI handles routine tasks and enforces secure coding standards. This synergy not only accelerates the development process but also ensures that security considerations are integral from the outset, minimizing risks and reducing the need for extensive revisions later on.
Testing Phase:
In the testing phase, AI-powered tools automate and enhance the detection of security flaws, making the process more efficient and thorough. There are tools that utilize AI and machine learning to perform comprehensive testing, including functional, performance, and security assessments.
These AI tools not only accelerate the testing process but also improve its effectiveness by simulating a wide range of scenarios and intelligently analyzing application behavior. They help ensure that vulnerabilities are identified and addressed before deployment, significantly reducing the risk of security incidents post-release.
Deployment Phase:
During deployment, AI systems play a crucial role in ensuring that software remains secure within its operational environment. AI-powered tools provide real-time monitoring, threat detection, and vulnerability management for applications, especially in cloud and containerized environments.
By incorporating these AI-driven tools into the deployment phase, organizations can proactively manage and mitigate security risks. Real-time monitoring and intelligent analysis ensure that applications are not only deployed efficiently but also safeguarded against emerging threats, maintaining the integrity and availability of services in production environments.
Maintenance and Monitoring Phase:
Post-deployment, AI offers continuous monitoring and swift response to security incidents, enhancing the overall security posture of the software. AI-powered tools play significant roles in this phase.
By integrating AI into maintenance and monitoring, organizations can significantly reduce the time between threat detection and response. AI systems process vast amounts of data faster than humanly possible, identifying and responding to threats in real-time. This continuous vigilance is crucial in today’s rapidly evolving threat landscape, where new vulnerabilities and attack methods emerge constantly.
Conclusion:
Integrating AI into the Secure Software Development Life Cycle enhances each phase by introducing efficiency, accuracy, and proactive security measures. From the initial gathering of requirements to the ongoing maintenance and monitoring post-deployment, AI-powered tools ensure that security is not an afterthought but a fundamental component of the software development process.
By leveraging AI in requirements gathering, organizations can accurately identify security needs and compliance requirements. In the design phase, AI aids in creating secure architectures by proactively identifying potential threats and recommending mitigation strategies. During development, AI assists in writing secure code and identifying vulnerabilities early on. In testing, AI automates and enhances the detection of security flaws, ensuring thorough examination before deployment. During deployment, AI provides real-time monitoring and threat detection, safeguarding the software in its operational environment. Finally, in maintenance and monitoring, AI offers continuous vigilance, swiftly identifying and responding to security incidents.
Adopting AI in the SSDLC not only strengthens the security posture of software products but also streamlines development processes, reduces costs associated with security breaches, and fosters a culture of security awareness. As cyber threats continue to evolve, the integration of AI into software development becomes increasingly essential for organizations aiming to protect their assets and maintain trust with their users.